Vật liệu:
-300g bơ lạt (Anchor)
-200g đường xay
-1trứng gà
-70g lòng trắng trứng
-1.5g muối Thái
-470g bột mì nổi (raisin flour)
-100g nho khô
-một ít lòng trắng trứng gà (để nhúng nho khô)
Cách làm
1. Bật lò cho nóng trước khoảng 10', lửa trên và dưới ở nhiệt độ 180 độ C
2. Ray bột mì và muối Thái
3. Ray đường xay
4. Cho bơ đánh với đường xay cho tới khi vừa mềm và mịn
5. Cho trứng và lòng trắng trứng vào đánh
6. Cho bột và muối Thái đã ray vào đánh chung
7. Cho hỗn hợp vào túi để nặn bánh
8. Nhúng nho khô vào lòng trắng và cho vào giữa bánh để làm nhân
9. Nướng ở 180 độ C trong khoảng 12-15'
10. Khi bánh chín để thật nguội và cho vào hộp kín trữ được khoảng 2 tuần
17 Nov 2012
31 Oct 2012
Cool Subnetting Tricks with VLSM
A few months back, I showed you how to organize your network into smaller subnets.
My post covered the details of the concept of subnetting. So if you
missed that article, I would suggest taking a look at it to make sure
you understand VLSM and this article in its entirety. For now, I will
assume that you are already familiar with subnetting and know how to
divide a network into smaller subnets.
In today’s article, we’ll subnet an already subnetted network into multiple subnets with variable subnet masks and then allocate them within our sample network.
Variable Length Subnet Mask (VLSM) is a key technology on large scalable networks. Mastering the concept of VLSM is not an easy task, but it’s well worth it. The importance of VLSM and its beneficial contribution to networking design is unquestionable. At the end of this article you will be able to understand the benefits of VLSM and describe the process of calculating VLSMs. I will use a real world example to help you understand the whole process and its beneficial effects.
Efficient use of IP addresses: IP addresses are allocated according to the host space requirement of each subnet.
IP addresses are not wasted; for example, a Class C network of 192.168.10.0 and a mask of 255.255.255.224 (/27) allows you to have eight subnets, each with 32 IP addresses (30 of which could be assigned to devices). What if we had a few WAN links in our network (WAN links need only one IP address on each side, hence a total of two IP addresses per WAN link are needed).
Without VLSM that would be impossible. With VLSM we can subnet one of the subnets, 192.168.10.32, into smaller subnets with a mask of 255.255.255.252 (/30). This way we end up with eight subnets with only two available hosts each that we could use on the WAN links.
The /30 subnets created are: 192.168.10.32/30, 192.168.10.36/30, 192.168.10.40/30, 192.168.10.44/30, 192.168.10.48/30, 192.168.10.52/30, 192.168.10.56/30 192.168.10.60/30.
Support for better route summarization: VLSM supports hierarchical addressing design therefore, it can effectively support route aggregation, also called route summarization.
The latter can successfully reduce the number of routes in a routing table by representing a range of network subnets in a single summary address. For example subnets 192.168.10.0/24, 192.168.11.0/24 and 192.168.12.0/24 could all be summarized into 192.168.8.0/21.
This specific network consists of 3 WAN links that are allocated a subnet address range each from the pool of available subnets. Obviously 30 IP address are wasted (28 host addresses) since they are never going to be used on the WAN links.

Create a small table with all of this information and use it to create your VLSM network. The following table shows the block sizes used for subnetting a Class C subnet.

Having this table in front of you is very helpful. For example, if you have a subnet with 28 hosts then you can easily see from the table that you will need a block size of 32. For a subnet of 40 hosts you will need a block size of 64.

Take a deep breath … we’re almost done. We have identified the necessary block sizes for our sample network.
The final step is to allocate the actual subnets to our design and construct our VLSM network. We will take into account that subnet-zero can be used in our network design, therefore the following solution will really allow us to save unnecessary addressing waste:

With VLSM we have occupied 140 addresses. Nearly half of the address space of the Class C network is saved. The address space that remains unused is available for any future expansion.
Isn’t that amazing? We have reserved a great amount of addresses for future use. Our sample network diagram is finalized as shown on the following diagram:

It’s not that difficult once you understand the process of block sizes and the way to allocate them within your design. Don’t forget that VLSM relates directly to the subnetting process, therefore mastering the subnetting process is a prerequisite for effectively implementing VLSM. And feel free to go through my subnetting articles a couple of times to get a hang of the whole process.
By Stelios Antoniou
http://www.trainsignal.com/blog/cisco-ccna-vlsm
In today’s article, we’ll subnet an already subnetted network into multiple subnets with variable subnet masks and then allocate them within our sample network.
Variable Length Subnet Mask (VLSM) is a key technology on large scalable networks. Mastering the concept of VLSM is not an easy task, but it’s well worth it. The importance of VLSM and its beneficial contribution to networking design is unquestionable. At the end of this article you will be able to understand the benefits of VLSM and describe the process of calculating VLSMs. I will use a real world example to help you understand the whole process and its beneficial effects.
Benefits of VLSM
VLSM provides the ability to subnet an already subnetted network address. The benefits that arise from this behavior include:Efficient use of IP addresses: IP addresses are allocated according to the host space requirement of each subnet.
IP addresses are not wasted; for example, a Class C network of 192.168.10.0 and a mask of 255.255.255.224 (/27) allows you to have eight subnets, each with 32 IP addresses (30 of which could be assigned to devices). What if we had a few WAN links in our network (WAN links need only one IP address on each side, hence a total of two IP addresses per WAN link are needed).
Without VLSM that would be impossible. With VLSM we can subnet one of the subnets, 192.168.10.32, into smaller subnets with a mask of 255.255.255.252 (/30). This way we end up with eight subnets with only two available hosts each that we could use on the WAN links.
The /30 subnets created are: 192.168.10.32/30, 192.168.10.36/30, 192.168.10.40/30, 192.168.10.44/30, 192.168.10.48/30, 192.168.10.52/30, 192.168.10.56/30 192.168.10.60/30.
Support for better route summarization: VLSM supports hierarchical addressing design therefore, it can effectively support route aggregation, also called route summarization.
The latter can successfully reduce the number of routes in a routing table by representing a range of network subnets in a single summary address. For example subnets 192.168.10.0/24, 192.168.11.0/24 and 192.168.12.0/24 could all be summarized into 192.168.8.0/21.
Address Waste Without VLSM
The following diagram shows a sample internetwork which uses a network C address 192.168.10.0 (/24) subnetted into 8 equal size subnets (32 available IP addresses each) to be allocated to the various portions of the network.This specific network consists of 3 WAN links that are allocated a subnet address range each from the pool of available subnets. Obviously 30 IP address are wasted (28 host addresses) since they are never going to be used on the WAN links.

Implementing VLSM
In order to be able to implement VLSMs in a quick and efficient way, you need to understand and memorize the IP address blocks and available hosts for various subnet masks.Create a small table with all of this information and use it to create your VLSM network. The following table shows the block sizes used for subnetting a Class C subnet.

Having this table in front of you is very helpful. For example, if you have a subnet with 28 hosts then you can easily see from the table that you will need a block size of 32. For a subnet of 40 hosts you will need a block size of 64.
Example: Create a VLSM Network
Let us use the sample network provided above to implement VLSM. According to the number of hosts in each subnet, identify the addressing blocks required. You should end up with the following VLSM table for this Class C network 192.168.10.0/24.
Take a deep breath … we’re almost done. We have identified the necessary block sizes for our sample network.
The final step is to allocate the actual subnets to our design and construct our VLSM network. We will take into account that subnet-zero can be used in our network design, therefore the following solution will really allow us to save unnecessary addressing waste:

With VLSM we have occupied 140 addresses. Nearly half of the address space of the Class C network is saved. The address space that remains unused is available for any future expansion.
Isn’t that amazing? We have reserved a great amount of addresses for future use. Our sample network diagram is finalized as shown on the following diagram:

Final Thoughts
Variable Length Subnet Mask is an extremely important chapter in Network Design. Honestly, if you want to design and implement scalable and efficient networks, you should definitely learn how to design and implement VLSM.It’s not that difficult once you understand the process of block sizes and the way to allocate them within your design. Don’t forget that VLSM relates directly to the subnetting process, therefore mastering the subnetting process is a prerequisite for effectively implementing VLSM. And feel free to go through my subnetting articles a couple of times to get a hang of the whole process.
By Stelios Antoniou
http://www.trainsignal.com/blog/cisco-ccna-vlsm
How to Organize Your Network Into Smaller Subnets
If you’re new to this field, I would suggest adding both Part 1 and Part 2: IP Routing Process to your reading list, since it provides some additional information that can be useful in getting a firm grasp of the subnetting concept.
In today’s article we are going to learn about the concept of subnetting and how we can use it to divide our classful network into smaller networks that can operate in separate working zones. We’ll also take a look at how we can conserve address space and save resources on process management with the use of subnetting.
I’ll use a few examples to clearly present the steps of subnetting and help you master this topic. And although at first this may seem difficult, don’t give up! All it takes is some time and practice!
What Is Subnetting?
Subnetting is the process of stealing bits from the HOST part of an IP address in order to divide the larger network into smaller sub-networks called subnets. After subnetting, we end up with NETWORK SUBNET HOST fields. We always reserve an IP address to identify the subnet and another one to identify the broadcast address within the subnet. In the following sections you will find out how all this is possible.Why Use Subnetting?
Conservation of IP addresses: Imagine having a network of 20 hosts. Using a Class C network will waste a lot of IP addresses (254-20=234). Breaking up large networks into smaller parts would be more efficient and would conserve a great amount of addresses.Reduced network traffic: The smaller networks created the smaller broadcast domains are formed hence less broadcast traffic on network boundaries.
Simplification: Breaking large networks into smaller ones could simplify fault troubleshooting by isolating network problems down to their specific existence.
The Subnetting Concept
You will be surprised how easy the concept of Subnetting really is. Imagine a network with a total of 256 addresses (a Class C network). One of these addresses is used to identify the network address and another one is used to identify the broadcast address on the network. Therefore, we are left with 254 addresses available for addressing hosts.If we take all these addresses and divide them equally into 8 different subnets we still keep the total number of original addresses, but we have now split them into 8 subnets with 32 addresses in each. Each new subnet needs to dedicate 2 addresses for the subnet and broadcast address within the subnet.
The result is that we eventually come up with 8 subnets, each one possessing 30 addresses available for hosts. You can see that the total amount of addressable hosts is reduced (240 instead of 254) but better management of addressing space is gained. I’ll now use a couple of examples to help explain the process of subnetting as clearly as possible.
Subnetting a Class C Address Using the Binary Method
We will use a Class C address which takes 5 bits from the Host field for subnetting and leaves 3 bits for defining hosts as shown in figure 1 below. Having 5 bits available for defining subnets means that we can have up to 32 (2^5) different subnets.It should be noted that in the past using subnet zero (00000—) and all-ones subnet (11111—) was not allowed. This is not true nowadays. Since Cisco IOS Software Release 12.0 the entire address space including all possible subnets is explicitly allowed.

Let’s use IP address 192.168.10.44 with subnet mask 255.255.255.248 or /29.
STEP 1: Convert to Binary

STEP 2: Calculate the Subnet Address
To calculate the Subnets IP Address you need to perform a bit-wise AND operation (1+1=1, 1+0 or 0+1 =0, 0+0=0) on the host IP address and subnet mask. The result is the subnet address in which the host is situated.
STEP 3: Find Host Range
We know already that for subnetting this Class C address we have borrowed 5 bits from the Host field. These 5 bits are used to identify the subnets. The remaining 3 bits are used for defining hosts within a particular subnet.The Subnet address is identified by all 0 bits in the Host part of the address. The first host within the subnet is identified by all 0s and a 1. The last host is identified by all 1s and a 0. The broadcast address is the all 1s. Now, we move to the next subnet and the process is repeated the same way. The following diagram clearly illustrates this process:

STEP 4: Calculate the Total Number of Subnets and Hosts Per Subnet
Knowing the number of Subnet and Host bits we can now calculate the total number of possible subnets and the total number of hosts per subnet. We assume in our calculations that all-zeros and all-ones subnets can be used. The following diagram illustrated the calculation steps.
Subnetting a Class C Address Using the Fast Way
Now let’s see how we can subnet the same Class C address using a faster method. Let’s again use the IP address 192.168.10.44 with subnet mask 255.255.255.248 (/29). The steps to perform this task are the following:1. Total number of subnets: Using the subnet mask 255.255.255.248, number value 248 (11111000) indicates that 5 bits are used to identify the subnet. To find the total number of subnets available simply raise 2 to the power of 5 (2^5) and you will find that the result is 32 subnets.
Note that if subnet all-zeros is not used then we are left with 31 subnets and if also all-ones subnet is not used then we finally have 30 subnets.
2. Hosts per subnet: 3 bits are left to identify the host therefore the total number of hosts per subnet is 2 to the power of 3 minus 2 (1 address for subnet address and another one for the broadcast address)(2^3-2) which equals to 6 hosts per subnet.
3. Subnets, hosts and broadcast addresses per subnet: To find the valid subnets for this specific subnet mask you have to subtract 248 from the value 256 (256-248=8) which is the first available subnet address.
Actually the first available one is the subnet-zero which we explicitly note. Next subnet address is 8+8=16, next one is 16+8=24 and this goes on until we reach value 248. The following table provides all the calculated information.
Note that our IP address (192.168.10.44) lies in subnet 192.168.10.40.

Test Your Subnetting Knowledge and Practice, Practice, Practice!
Don’t get discouraged if you didn’t understand every little detail I went over in this article. Subnetting is not really that difficult, but it does require a bit of practice.Start with testing your knowledge of subnets and make sure you feel confident about this before you move on to designing your own subnets. But remember, if you’re on the Cisco Networking track you will have to deal with subnetting sooner or later, so grab this opportunity and start testing yourself.
Go ahead and subnet the network address 192.168.10.0 address using the subnet mask 255.255.255.192 (/26). Find the valid subnets, host ranges and broadcast addresses per subnet. If you want to double-check your answer, feel free to leave me a comment and I will provide you with the correct solution.
By Stelios Antoniou
http://www.trainsignal.com/blog/simplify-routing-how-to-organize-your-network-into-smaller-subnets
23 Oct 2012
Yorkshire Pudding
4 oz (100g) Plain Flour
1 medium sized egg
Pinch of salt
½ pint (280ml) of milk (or mixture of milk and water)
2oz
(50g) lard/fat or 2 tablespoons of oil
Mix the flour and salt in a basin and make a hollow in
middle. Drop the egg into the hollow and stir in with a wooden spoon. Add the
milk (milk and water) gradually, stirring all of the time until the flour is
worked in. Add rest of liquid and beat well. The end result should have a
similar consistency to single cream.
Melt the fat in cooking tin until spitting hot.(top of
the oven) Can be one large tin square, rectangular, round or small tins or a
bun tin. When the fat is hot enough pour in the batter just half filling small
tins, patty tins or bun tins. Cook at 230C or gas mark 8. Large tins for
about 30 minutes, small tins or bun tins 15 – 20 minutes.
When cooked they should turn out puffy, golden and crispy
on the outside and sunken in the middle.
By Lorraine Waddington
18 Sept 2012
EMC does not start
EMC has error when launching
The attempt to connect to http://exch01.domain.local/powershell using "KERBEROS" authentication failed: connecting to remote server failed with following error message: access is denied
1. Check all services make sure they are all started
2. Check the time and time zone, make sure it synchronized with DC
Lauch EMC, if it still does not work go to the next steps
3. From exchange server open a command prompt and type
WinRM QuickConfig
Answer "y" or yes to all prompts.
Keep running the above command until it returns a positive result.
(WinRM already set up to receive......blah, blah, blah)
4. After that returns a similar message as above, set they are set to start Default
Windows Remote Management (WS-Management)
World Wide Web Publishing Service.
5. Run IIS Manager. Click on the "Default Site" and select restart
Good luck
10 Sept 2012
Tip: 7 Best Practices for Physical Servers Hosting Hyper-V Roles
http://technet.microsoft.com/en-us/magazine/dd744830.aspx
Before setting up a physical server to host the Hyper-V role, download,
read, and understand information included in the white paper
“Performance Tuning Guidelines for Windows Server 2008”.
Three sections in this white paper that can have a significant impact
on the performance of the physical server discuss tuning the server
hardware and setting up the networking and storage subsystems. These are
especially critical for Hyper-V because the hypervisor itself sits on
top of the hardware layer as described earlier and controls all hardware
in Windows Server 2008. The operating system itself essentially runs in
a virtual machine, better known as the Parent Partition.
Here are seven best practices for physical servers hosting the Hyper-V role.
Avoid Overloading the Server
Determining the number of virtual machines that will be hosted on the Hyper-V server and the workloads they will be handling is critical. The version of the operating system that will be installed on the physical server can help in this regard, so the first “best practice” is to consider using Windows Server 2008 Datacenter x64 with Hyper-V. The Datacenter x64 edition supports up to 64 processors, 2 terabytes of physical memory, and 16 failover cluster nodes for Quick Migration scenarios and allows unlimited virtual machines to be run in Hyper-V. Selecting a Server Core installation provides added benefits, including enhanced security and lower maintenance.
Determining the number of virtual machines that will be hosted on the Hyper-V server and the workloads they will be handling is critical. The version of the operating system that will be installed on the physical server can help in this regard, so the first “best practice” is to consider using Windows Server 2008 Datacenter x64 with Hyper-V. The Datacenter x64 edition supports up to 64 processors, 2 terabytes of physical memory, and 16 failover cluster nodes for Quick Migration scenarios and allows unlimited virtual machines to be run in Hyper-V. Selecting a Server Core installation provides added benefits, including enhanced security and lower maintenance.
Ensure High-Speed Access to Storage
For storage, consider using a storage area network (SAN) that is configured with highspeed (10,000 rpms or greater) drives (SATA or SAS) that support queued I/O and Raid 0 +1 configurations. You can use either Fibre Channel or iSCSI SAN hardware.
For storage, consider using a storage area network (SAN) that is configured with highspeed (10,000 rpms or greater) drives (SATA or SAS) that support queued I/O and Raid 0 +1 configurations. You can use either Fibre Channel or iSCSI SAN hardware.
Install Multiple Network Interface Cards
For networking, be sure to have more than one network card installed on the physical server and dedicate one network interface to Hyper-V server administration. This means no virtual networks in Hyper-V will be configured to use this NIC. For high-workload virtual machines, you might want to dedicate a physical network adapter on the server to the virtual network the virtual machine is using. Ensure virtual machines that share a physical adapter do not oversubscribe to the physical network. Use the Reliability And Performance Monitor to establish a performance baseline for the load and then adjust NIC configurations and loads accordingly.
For networking, be sure to have more than one network card installed on the physical server and dedicate one network interface to Hyper-V server administration. This means no virtual networks in Hyper-V will be configured to use this NIC. For high-workload virtual machines, you might want to dedicate a physical network adapter on the server to the virtual network the virtual machine is using. Ensure virtual machines that share a physical adapter do not oversubscribe to the physical network. Use the Reliability And Performance Monitor to establish a performance baseline for the load and then adjust NIC configurations and loads accordingly.
If you have only a single NIC in the machine that you are configuring
the Hyper-V role on and you are doing the configuration remotely (say,
in an RDP session) if you choose to bind the Virtual Switch Protocol to
the single NIC in the machine, you will be disconnected from your
session and a reconnection might not be possible until the newly created
virtual network adapter has been properly configured.
Avoid Mixing Virtual Machines That Can Use Integration Services with Those That Cannot
Do not mix on the same physical server virtual machines that can take advantage of Hyper-V Integration Services with those that cannot. Virtual machines that cannot use Integration Services must use legacy network adapters to gain access to the physical network. To accommodate legacy network adapters, you might need to disable some high-end features on the network interface, which can unnecessarily limit the functionality of the synthetic devices. Additionally, using emulated devices places an extra workload on the Hyper-V server.
Do not mix on the same physical server virtual machines that can take advantage of Hyper-V Integration Services with those that cannot. Virtual machines that cannot use Integration Services must use legacy network adapters to gain access to the physical network. To accommodate legacy network adapters, you might need to disable some high-end features on the network interface, which can unnecessarily limit the functionality of the synthetic devices. Additionally, using emulated devices places an extra workload on the Hyper-V server.
Configure Antivirus Software to Bypass Hyper-V Processes and Directories
If you are running antivirus software on the physical server, you might want to consider excluding the Vmms.exe and Vmswp.exe processes. Also, exclude the directories that contain the virtual machine configuration files and virtual hard disks from active scanning. An added benefit of using pass-through disks in your virtual machines is that you can use the antivirus software running on the physical server to protect that virtual machine.
If you are running antivirus software on the physical server, you might want to consider excluding the Vmms.exe and Vmswp.exe processes. Also, exclude the directories that contain the virtual machine configuration files and virtual hard disks from active scanning. An added benefit of using pass-through disks in your virtual machines is that you can use the antivirus software running on the physical server to protect that virtual machine.
Avoid Storing System Files on Drives Used for Hyper-V Storage
Do not store any system files (Pagefile.sys) on drives dedicated to storing virtual machine data.
Do not store any system files (Pagefile.sys) on drives dedicated to storing virtual machine data.
Monitor Performance to Optimize and Manage Server Loading
When running multiple high-workload virtual machines on a Hyper-V server, ensure a proper aggregate performance baseline is obtained over a specified period of time (say, five days during normal working hours) to ensure the hardware configuration for the physical server is optimal to support the load being placed on it by the virtual machines. If adding more memory, processors, or higher performing storage is not possible, you might need to migrate the virtual machines to other Hyper-V servers.
When running multiple high-workload virtual machines on a Hyper-V server, ensure a proper aggregate performance baseline is obtained over a specified period of time (say, five days during normal working hours) to ensure the hardware configuration for the physical server is optimal to support the load being placed on it by the virtual machines. If adding more memory, processors, or higher performing storage is not possible, you might need to migrate the virtual machines to other Hyper-V servers.
9 Sept 2012
Raid 10 on x3650M4 with ServerRaid M5510e
It will be easier if raid setup can be done in ServerGuide but unfortunately at the time I was writing this post ServerGuide 9.23 did not work with my x3650 M4 7915.
1. Turn on the server and press F1 at the IBM startup screen.
2. Select Server Settings - Adapter and UEFI drivers then press Enter (to compile the list of drivers)
3. Select the type of Raid card which is in your server
4. You will have 2 options EFI WebBios and EFI CLI . Select option 1 EFI WebBios
5. Select your raid card and click Start
6. Select Configuration Wizard at MegaRaid Bios Config Utility screen.
2. Select Server Settings - Adapter and UEFI drivers then press Enter (to compile the list of drivers)
3. Select the type of Raid card which is in your server
4. You will have 2 options EFI WebBios and EFI CLI . Select option 1 EFI WebBios
5. Select your raid card and click Start
6. Select Configuration Wizard at MegaRaid Bios Config Utility screen.
7. Select New Configuration then Manual Congiguration and click Next
8. Select DriveGroup0 on the right pane (DriveGroups) and select half of physical disk on the left pane (Drives) and click Add to Array.
9. Click Accept DG. MegaRaid will display another drive group DriveGroup1
10. Select new DriveGroup1 on the right pane then select the rest hard disk on the left pane and click on Add to Array.
10. Select new DriveGroup1 on the right pane then select the rest hard disk on the left pane and click on Add to Array.
11. Click Accept DG. In the right pane you will have 3 drivegroups but only 2 has size displayed. The size of dirvegroup is the size of your hard disk.
12. Click Next.
13. In the Span Definition screen select each of DriveGroup in the combo box and click Add to Span.
13. In the Span Definition screen select each of DriveGroup in the combo box and click Add to Span.
14. Click Next.
15. If the type of Raid is 10 that means you do thing right. Click Update Size and then Accept.
16. The next screen will display Raid level of every drivegroup. In my case it is Raid0.
17. Click Next then Accept to finish
17. Click Next then Accept to finish
Good luck :-)
ServeRaid M5110e on x3650M4
Unfortunately at the time I am installing Windows 2008 R2 on x3650M4 (7915) IBM has not yet updated ServeRaid M5110e on its ServerGuide 9.23. Whatever raid level I selected by following steps in ServerGuide the critical error of raid update failure displayed. It takes me a day before realizing that I need to find a way round.
First of all the raid setting have to be done via WebRaid because ServerGuide raid setup did not work.
Secondly find out RaidServe M5110e windows driver at http://download2.boulder.ibm.com/sar/CMA/XSA/ibm_dd_sraidmr_5.2.127_windows_32-64.exe and copy it in to USB key
Lastly restart 3650M4 by Windows 2008 R2 DVD and setup as normally except had to upload ServeRaid driver from the USB key before able to see the hard disk partition.
...Go for a beer now
First of all the raid setting have to be done via WebRaid because ServerGuide raid setup did not work.
Secondly find out RaidServe M5110e windows driver at http://download2.boulder.ibm.com/sar/CMA/XSA/ibm_dd_sraidmr_5.2.127_windows_32-64.exe and copy it in to USB key
Lastly restart 3650M4 by Windows 2008 R2 DVD and setup as normally except had to upload ServeRaid driver from the USB key before able to see the hard disk partition.
...Go for a beer now
22 Aug 2012
Understanding where your virtual machine files are [Hyper-V]
http://blogs.msdn.com/b/virtual_pc_guy/archive/2010/03/10/understanding-where-your-virtual-machine-files-are-hyper-v.aspx
To be honest, I am surprised that I have not blogged about this
before, but today I would like to talk about how virtual machine files
are placed on the hard disk.
Virtual Machine files
The first thing to know is what files are used to create a virtual machine:
Hyper-V has a concept of the “virtual machine data root” and the “virtual machine snapshot root”. These are the locations where the virtual machine configuration (.XML) and saved state (.BIN & .VSV) files are stored. For example – a virtual machine which had a virtual machine data root of “D:\Foo” and a snapshot data root of “D:\Foo” and had two snapshots would have a file structure like this:
D:\Foo
D:\Foo\Snapshots
D:\Foo\Snapshots\[Snapshot #1 GUID directory]
D:\Foo\Snapshots\[Snapshot #1 GUID].XML
D:\Foo\Snapshots\[Snapshot #2 GUID directory]
D:\Foo\Snapshots\[Snapshot #2 GUID].XML
D:\Foo\Virtual Machines
D:\Foo\Virtual Machines\[Virtual Machine GUID directory]
D:\Foo\Virtual Machines\[Virtual Machine GUID].XML
If the snapshots and the virtual machine had saved states associated with them – then the file structure would look like this:
D:\Foo
D:\Foo\Snapshots
D:\Foo\Snapshots\[Snapshot #1 GUID directory]
D:\Foo\Snapshots\[Snapshot #1 GUID directory]\[Snapshot #1 GUID].BIN
D:\Foo\Snapshots\[Snapshot #1 GUID directory]\[Snapshot #1 GUID].VSV
D:\Foo\Snapshots\[Snapshot #1 GUID].XML
D:\Foo\Snapshots\[Snapshot #2 GUID directory]
D:\Foo\Snapshots\[Snapshot #2 GUID directory]\[Snapshot #1 GUID].BIN
D:\Foo\Snapshots\[Snapshot #2 GUID directory]\[Snapshot #1 GUID].VSV
D:\Foo\Snapshots\[Snapshot #2 GUID].XML
D:\Foo\Virtual Machines
D:\Foo\Virtual Machines\[Virtual Machine GUID directory]
D:\Foo\Virtual Machines\[Virtual Machine GUID directory]\[Virtual Machine GUID].BIN
D:\Foo\Virtual Machines\[Virtual Machine GUID directory]\[Virtual Machine GUID].VSV
D:\Foo\Virtual Machines\[Virtual Machine GUID].XML
Some key things to highlight about data roots:
.VHD files can be created pretty much anywhere you want. In Windows Server 2008 R2, .AVHD files are always created in the same location as their parent .VHD files.
Common Virtual Machine File Configuration #1 – Default Virtual Machine Data Root
A virtual machine with a default virtual machine data root is one where you created the virtual machine and accepted the default options in the new virtual machine wizard, specifically where you did not check to “Store the virtual machine in a different location” on the first page of the new virtual machine wizard:

In this configuration option the virtual machine data root and snapshot data root will be set to the path specified under the Hyper-V Settings in the “Virtual Machines” setting, and the virtual hard disk will be created under the path specified under the Hyper-V Settings in the “Virtual Hard Disks” setting:

These paths are normally set to “C:\ProgramData\Microsoft\Windows\Hyper-V” for the “Virtual Machines” setting and “C:\Users\Public\Documents\Hyper-V\Virtual Hard Disks” for the “Virtual Hard Disks” setting. That said – I usually change these settings to “D:\Hyper-V\Configuration Files” and “D:\Hyper-V\Virtual Hard Disks” on my systems as I find this easier to work with.
Common Virtual Machine File Configuration #2 – External Virtual Machine Data Root
If you do select to “Store the virtual machine in a different location” you will get what we call a virtual machine with an external virtual machine data root.

With this option we create a new folder named after the virtual machine, and set the virtual machine data root and snapshot data root to this folder. We also default to creating the virtual hard disk in this new folder.
Common Virtual Machine File Configuration #3 – Exported / Imported virtual machine
If you export a virtual machine a virtual machine and then import it without checking the option to “Duplicate all files so the same virtual machine can be imported again”, you will end up with a virtual machine that looks like a virtual machine with an external data root – but there will be one difference.

Instead of having the virtual hard disks stored in the same location as the virtual machine data root – they will be stored in a “Virtual Hard Disks” folder under the virtual machine data root folder instead.
Changing a virtual machine to a default data root virtual machine
If you have an existing virtual machine that you want to change to a “default data root” configuration – the easiest way to do this is to export the virtual machine and then import it and check the option to “Duplicate all files so the same virtual machine can be imported again”. The resulting virtual machine will be a default data root virtual machine.
Changing a virtual machine to an external data root virtual machine
If you have an existing virtual machine that you want to change to an “external data root” configuration, you have two options:
The only way to change the virtual machine data root for a virtual machine is by using import / export. But the snapshot data root for a virtual machine can be changed at any time – as long as all snapshots are deleted first. If you have deleted all existing snapshots you can change the snapshot data root by changing the “Snapshot File Location” setting for the virtual machine under the virtual machine settings user interface.
Virtual Machine files
The first thing to know is what files are used to create a virtual machine:
- .XML files
- These files contain the virtual machine configuration details. There is one of these for each virtual machine and each snapshot of a virtual machine. They are always named with the GUID used to internally identify the virtual machine or snapshot in question.
- .BIN files
- This file contains the memory of a virtual machine or snapshot that is in a saved state.
- .VSV files
- This file contains the saved state from the devices associated with the virtual machine.
- .VHD files
- These are the virtual hard disk files for the virtual machine
- .AVHD files
- These are the differencing disk files used for virtual machine snapshots
Hyper-V has a concept of the “virtual machine data root” and the “virtual machine snapshot root”. These are the locations where the virtual machine configuration (.XML) and saved state (.BIN & .VSV) files are stored. For example – a virtual machine which had a virtual machine data root of “D:\Foo” and a snapshot data root of “D:\Foo” and had two snapshots would have a file structure like this:
D:\Foo
D:\Foo\Snapshots
D:\Foo\Snapshots\[Snapshot #1 GUID directory]
D:\Foo\Snapshots\[Snapshot #1 GUID].XML
D:\Foo\Snapshots\[Snapshot #2 GUID directory]
D:\Foo\Snapshots\[Snapshot #2 GUID].XML
D:\Foo\Virtual Machines
D:\Foo\Virtual Machines\[Virtual Machine GUID directory]
D:\Foo\Virtual Machines\[Virtual Machine GUID].XML
If the snapshots and the virtual machine had saved states associated with them – then the file structure would look like this:
D:\Foo
D:\Foo\Snapshots
D:\Foo\Snapshots\[Snapshot #1 GUID directory]
D:\Foo\Snapshots\[Snapshot #1 GUID directory]\[Snapshot #1 GUID].BIN
D:\Foo\Snapshots\[Snapshot #1 GUID directory]\[Snapshot #1 GUID].VSV
D:\Foo\Snapshots\[Snapshot #1 GUID].XML
D:\Foo\Snapshots\[Snapshot #2 GUID directory]
D:\Foo\Snapshots\[Snapshot #2 GUID directory]\[Snapshot #1 GUID].BIN
D:\Foo\Snapshots\[Snapshot #2 GUID directory]\[Snapshot #1 GUID].VSV
D:\Foo\Snapshots\[Snapshot #2 GUID].XML
D:\Foo\Virtual Machines
D:\Foo\Virtual Machines\[Virtual Machine GUID directory]
D:\Foo\Virtual Machines\[Virtual Machine GUID directory]\[Virtual Machine GUID].BIN
D:\Foo\Virtual Machines\[Virtual Machine GUID directory]\[Virtual Machine GUID].VSV
D:\Foo\Virtual Machines\[Virtual Machine GUID].XML
Some key things to highlight about data roots:
- We always create a “Virtual Machines” folder under the virtual machine data root and store the virtual machine configuration files there.
- We always create a “Snapshots” folder under the snapshot data rot and store the snapshot configuration files there.
- We fully support multiple virtual machines having the same virtual machine and snapshot data root
.VHD files can be created pretty much anywhere you want. In Windows Server 2008 R2, .AVHD files are always created in the same location as their parent .VHD files.
Common Virtual Machine File Configuration #1 – Default Virtual Machine Data Root
A virtual machine with a default virtual machine data root is one where you created the virtual machine and accepted the default options in the new virtual machine wizard, specifically where you did not check to “Store the virtual machine in a different location” on the first page of the new virtual machine wizard:

In this configuration option the virtual machine data root and snapshot data root will be set to the path specified under the Hyper-V Settings in the “Virtual Machines” setting, and the virtual hard disk will be created under the path specified under the Hyper-V Settings in the “Virtual Hard Disks” setting:

These paths are normally set to “C:\ProgramData\Microsoft\Windows\Hyper-V” for the “Virtual Machines” setting and “C:\Users\Public\Documents\Hyper-V\Virtual Hard Disks” for the “Virtual Hard Disks” setting. That said – I usually change these settings to “D:\Hyper-V\Configuration Files” and “D:\Hyper-V\Virtual Hard Disks” on my systems as I find this easier to work with.
Common Virtual Machine File Configuration #2 – External Virtual Machine Data Root
If you do select to “Store the virtual machine in a different location” you will get what we call a virtual machine with an external virtual machine data root.

With this option we create a new folder named after the virtual machine, and set the virtual machine data root and snapshot data root to this folder. We also default to creating the virtual hard disk in this new folder.
Common Virtual Machine File Configuration #3 – Exported / Imported virtual machine
If you export a virtual machine a virtual machine and then import it without checking the option to “Duplicate all files so the same virtual machine can be imported again”, you will end up with a virtual machine that looks like a virtual machine with an external data root – but there will be one difference.

Instead of having the virtual hard disks stored in the same location as the virtual machine data root – they will be stored in a “Virtual Hard Disks” folder under the virtual machine data root folder instead.
Changing a virtual machine to a default data root virtual machine
If you have an existing virtual machine that you want to change to a “default data root” configuration – the easiest way to do this is to export the virtual machine and then import it and check the option to “Duplicate all files so the same virtual machine can be imported again”. The resulting virtual machine will be a default data root virtual machine.
Changing a virtual machine to an external data root virtual machine
If you have an existing virtual machine that you want to change to an “external data root” configuration, you have two options:
- Spend some time scripting the import / export APIs in Hyper-V. It is possible to do it this way – but it is not easy.
- Move the virtual machine using System Center Virtual Machine Manager. SCVMM will always transform a virtual machine into an external data root virtual machine in the process of moving it.
The only way to change the virtual machine data root for a virtual machine is by using import / export. But the snapshot data root for a virtual machine can be changed at any time – as long as all snapshots are deleted first. If you have deleted all existing snapshots you can change the snapshot data root by changing the “Snapshot File Location” setting for the virtual machine under the virtual machine settings user interface.
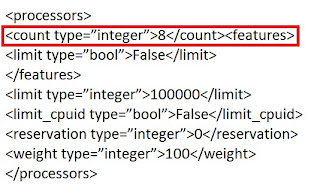
Hyper-V CPU limitation
By
default Hyper-V only allows max 4 CPU core to be displayed on VM. To
get the highest core available in your Hyper V host displayed on VM you simply edit count type value in VM
config xml file and ...enjoy your work.
Subscribe to:
Posts (Atom)